Can Someone Hack Your Phone By Calling Or Texting You will be explained in this post. Does receiving a dubious call or text indicate that your device has been compromised already? Probably not, although it might be the beginning of a fraudulent scam or hacking effort. Continue reading to learn what to do if a hacker calls so you can protect your phone. Next, to help guard against phone hacking and other dangerous techniques scammers’ use, install Avast One.
Can Someone Hack Your Phone By Calling Or Texting You
In this article, you can know about Can Someone Hack Your Phone By Calling Or Texting You here are the details below;
- Academy: Is It Possible for Someone to Hack Your Phone by Calling or Texting You?
- Composed by Anthony Freda
- Posted on September 11, 2023
Can someone hack into your phone by calling you?
It is improbable that phone hacking originate directly from phone calls. However, calls and texts can be used to initiate phishing attacks or other scams to deceive you into giving over private information, transferring money, or downloading viruses or spyware. Text messages can also include malware.
This Article Contains:
- Is it possible for someone to call you via a phone hack?
- Can someone text me and gain access to my phone?
- A zero-click exploit is what?
- What additional techniques exist for breaking into my phone?
- How can I stop hackers from accessing my phone?
- Use Avast FAQs to provide protection against phone hacking.
The best defense against text and phone hacks is to never answer unknown numbers. Refrain from returning their calls or texts, and avoid clicking any links. Calling back could cost you at an international rate if you fall prey to a call-back scam, with the hacker keeping some or all of the money. Additionally, be wary of the social engineering techniques used by con artists to trick you into clicking a harmful link.
- One of the following messages could include a dubious link:
- An offering or a selling advertisement
- An appeal for assistance from a relative
Facebook or another social media platform is issuing a warning.
Hackers are able to “spoof” or mimic phone numbers and email addresses. Refrain from falling for it. Hackers frequently pose as reputable companies while making fraudulent phone calls in an attempt to trick victims into divulging personal information; this tactic is called vishing (voice phishing).
Scammers can pose as reputable companies over the phone in the hopes of getting their victim to provide personal information.Scammers can pose over the phone as representatives of a reliable company.
Can someone use an app to call you and then hack into your phone? Unanswered phone calls have previously allowed hackers to compromise WhatsApp users, but that security hole has now been fixed. Nevertheless, it’s hard to be completely safe because different kinds of hackers are constantly searching for fresh security holes. Generally speaking, the best you can do is maintain proactive online security and privacy management together with excellent digital hygiene.
Can spam calls hack your phone?
Because signals from cellular service providers aren’t able to hack phones directly, spam calls can’t hack your phone. However, the threat comes from spam calls that try to lure you into disclosing personal information.
So, is it possible to hack your phone by taking a call? No, but the FTC has alerted people to a new phone threat: deep fakes. In these scams, con artists impersonate you over the phone by using artificial intelligence (AI) or other digital technologies to clone your voice. They then pose as you and demand money from the victim.
Additionally, if you’ve had a lengthy conversation with a spammer posing as an official organization, they may use the information they obtain against you, potentially even using it to steal your phone number through a SIM swap hoax. These calls should not be trusted, and you should understand how to prevent phone spoofing.
How about “no caller ID” hacks, as they are called? Calls with “no caller ID” are just calls from private lines; they are not hacker calls. Can a phone be hacked by spam calls? Very unlikely. Scammers obtain you by requiring you to pick up and interact with them.
Additionally, be wary of unknown texts. Never click on a tie in a text message unless you were the one who started the conversation (e.g., by asking to change your password). There’s a rationale behind the term “phishing.” You won’t fall for the bait if you refuse to take it.
What distinguishes a fraud from a spam? Not only are phishing scam calls irritating, but they can also be scam calls that attempt to obtain your credit card information in addition to their usual one-time payment request. The same should be your approach to both kinds of calls: disregard them.
Phishing is frequently used in scam calls, but spam calls might merely be obnoxious, continuous sales calls.While spam calls are mostly only bothersome, phishing calls are always malevolent.
Can someone hack into my phone by texting me?
You cannot be hacked just by texting someone (unless they have access to advanced zero-click exploit technologies). Generally speaking, there is little risk as long as you do not open attachments or click any links. You should only open an attachment and click a link if you are certain it is safe and are expecting it.
Text message scammers send out a lot of texts. For the campaign to be effective, only a tiny portion of victims must click the text link. The victims can inadvertently download malware or be sent to a dangerous website where they have to enter personal data.
Can someone please SMS me to get access to my phone? usually just when you open an attachment or click a link. Even Jeff Bezos was once the victim of such a ploy, so don’t imagine you’re immune to them. Everyone experiences fatigue occasionally. Unwanted text messages are annoying, and they may cause you to become reckless. Fortunately, you can turn them off.
Can you get hacked by replying to a text?
Simply responding to an SMS message won’t get you hacked. On the other hand, the likelihood of being hacked increases if you interact with a hacker in any manner. They’ll figure out a way to trick you into clicking a link, which is how you end up getting hacked.
If you enter a message and hit submit, nothing happens in the background. However, the hacker already has more information about you and could fool you into sending them a link or other information. It’s preferable to stay completely silent.
What is a zero-click exploit?
An uncommon kind of hack that can target you without your intervention is a zero-click exploit. It won’t even occur to you that something is amiss. Since a zero-click attack needs to be quite sophisticated, it is unlikely that the typical person will be the target.
While they differ greatly from zero-day attacks, they are comparable in that it is very difficult to predict or stop them. Using a decent antivirus program and keeping your system and software updated are your best lines of defense.
The WhatsApp missed call hack, which placed spyware on phones without the user’s knowledge or consent, is one instance of a zero-click assault. These kinds of intrusions are significant enough security breaches to warrant media attention.
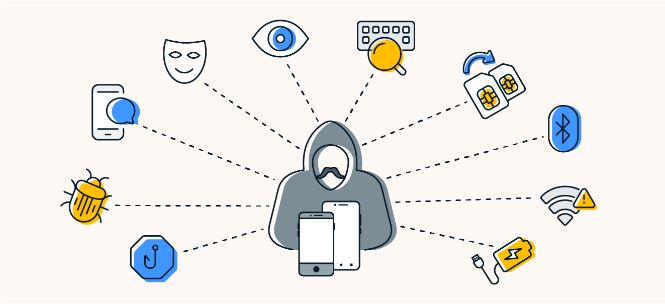
What other methods can be used to hack into my phone?
There are numerous ways for you to become hacked. While some might be easily avoided with common sense online browsing, others can be more difficult. Here are a few methods of phone hacking:
- Phishing: Phishing attacks, such as spear phishing, present a malicious text as authentic. The fraudster may ask for your password or attempt to get you to click on a link, and it may appear as though it is from the IRS or Amazon. Recall that respectable businesses and institutions will never SMS you for personal information. Also check graphic design software solutions
- Malvertising: Website advertisements may include code that infects your machine with malware. Although advertisements for gambling and pornographic content are more common on websites, big websites like the BBC and the New York Times have been targeted by malvertising in the past.
- Smishing: This kind of assault blends the terms “phishing” and “SMS.” When you get a text, you could be happy to see it and assume it’s from a friend who just got a new phone. However, your information could be compromised if you follow the link.
- Pretexting: Pretexting is creating an excuse or justification for you to act in a certain way either now or later. In order to get your trust and deceive you into transferring money, downloading malware, or disclosing personal information, the fraudster fabricates a story.
- Man-in-the-middle attacks: When a hacker gets in the way of you or another user and an application, they can intercept data. Usually, the intention behind these assaults is to steal personal data, such as praise card numbers or login credentials.
- Keylogging: The hacker can monitor the keystrokes you make while tapping your phone if they have installed a keylogger on it. Important facts including text message details, login credentials, and other personal information may be revealed in this method.
- SIM swapping: When a con artist persuades your mobile phone provider to provide a new SIM, this kind of fraud takes place. Their goal is to gain access to accounts that have been set up with two-factor authentication when they activate it. They will then receive the verification code on their phone as long as they are aware of the log-in credentials.
- Bluetooth: Hackers can access your phone by using software to intercept a Bluetooth connection. Never pair your phone at an untrusted environment or with an unknown device.
- Wi-Fi: Use additional caution when using public Wi-Fi because unprotected networks allow hackers to easily intercept your communications. When using public Wi-Fi on your phone for web surfing, texting, or making calls, always utilize a VPN.
- Public charging stations are susceptible to malware infection by hackers. Your private information may be collected if you connect your phone because this could spread to your device.
How are phones hacked by hackers? It appears as though fresh approaches are developed daily. Additionally, keep in mind that scam texts or calls can appear real, so you should always exercise caution when answering texts or calls.
How can I prevent my phone from being hacked?
The greatest defense against phone hacking is to install robust security software from a reliable provider. You can go a long way with wise browsing practices, but to protect you against threats you can’t see with your naked eye or anticipate, you’ll need stronger security.
It’s possible that you answered a seemingly harmless text asking for your date of birth, and that was the final piece of information a scammer needed to take your identity. Identity theft is a nightmare, so do your best to minimize the damage by keeping an eye out for phishing schemes and telltale signals of a phone hack.
Alternatively, you can utilize a software that will be many steps ahead of you, such as Avast BreachGuard. BreachGuard will notify you if one of your passwords appears in a data breach so you can change it right away and safeguard your account. In the unlikely event that your credentials or personal data have spilled, it even searches the black web for them. Also check crowd management software
The first thing you should do if you suspect your phone has been compromised is turn it off from the internet and do an anti-malware scan. If you ever find yourself in this situation, learn how to empty viruses from your iPhone or Android device; ideally, you should install protection software beforehand.
Help protect against phone hacking with Avast
Although dubious relationships can be avoided, what happens when security breaches occur covertly? The award-winning security and privacy features of Avast One will help protect your phone from hackers in real time, identify and stop malware before it can infect your device, and even alert you to links and downloads that could be harmful. Install it now for no cost.
FAQs
Can someone hack my iPhone?
iPhones are not exempt from internet hacking, nor can any other gadget. Watch out for warning indications such as unexpected phone calls or text messages, apps showing up on your iPhone that you didn’t install, pop-up windows that appear more frequently than usual, and notifications indicating that you’re using more data than usual. Always use reputable anti-malware software to safeguard your iPhone from threats like spyware.
Can someone hack my phone from my number?
Although some zero-click attacks can install malware even if you don’t accept calls or click texts, your phone cannot be compromised only by its number. Scammers typically need their victims to take an action, such as clicking on a malicious link or downloading an infected software, in order to hack a phone.
Can someone hack your phone number?
A data breach is one of the most popular ways for hackers to obtain your phone number. The information obtained—which may include anything from your Social Security number to your phone number—is frequently traded or sold on the dark web. It will be simpler for a hacker to access your internet accounts or employ focused social engineering techniques the more information they have about you.






Add Comment